Annotation
- Introduction
- Understanding Modern Face Recognition Systems
- The Technical Challenge of Masked Face Recognition
- Addressing Bias in Facial Recognition Systems
- Building a Masked Face Recognition Model
- Real-World Applications and Implementation Considerations
- Ethical Considerations and Responsible Deployment
- Pros and Cons
- Conclusion
- Frequently Asked Questions
Masked Face Recognition Guide: Build AI Systems That Work With Facial Coverings
Comprehensive guide on developing AI systems for accurate face recognition with masks, covering technical implementation, bias mitigation, and

Introduction
In today's evolving security landscape, face recognition technology faces unprecedented challenges with the widespread adoption of facial coverings. This comprehensive guide explores how to build robust AI systems capable of accurately identifying individuals even when they're wearing masks. We'll walk through practical steps using pre-trained models and accessible datasets, providing both technical depth and real-world applicability for developers and security professionals working with computer vision technologies.
Understanding Modern Face Recognition Systems
Face recognition represents a sophisticated biometric technology that identifies or verifies individuals from digital images or video frames. The process involves multiple stages: face detection, feature extraction, and classification. These systems analyze unique facial patterns and characteristics to create digital signatures that distinguish one person from another. The technology has become increasingly prevalent across security systems, mobile device authentication, and access control applications. The emergence of masked faces presents significant technical hurdles, as traditional systems rely on full facial visibility for optimal performance. Modern solutions must adapt to handle partial occlusions while maintaining accuracy and reliability in real-world scenarios.

The fundamental challenge lies in developing algorithms that can extract meaningful features from limited visible facial regions. Advanced systems now incorporate specialized training techniques using diverse datasets containing both masked and unmasked faces. This approach enables models to learn robust representations that remain effective even when significant portions of the face are obscured. Understanding these core principles is essential for anyone implementing computer vision tools in security or identification applications.
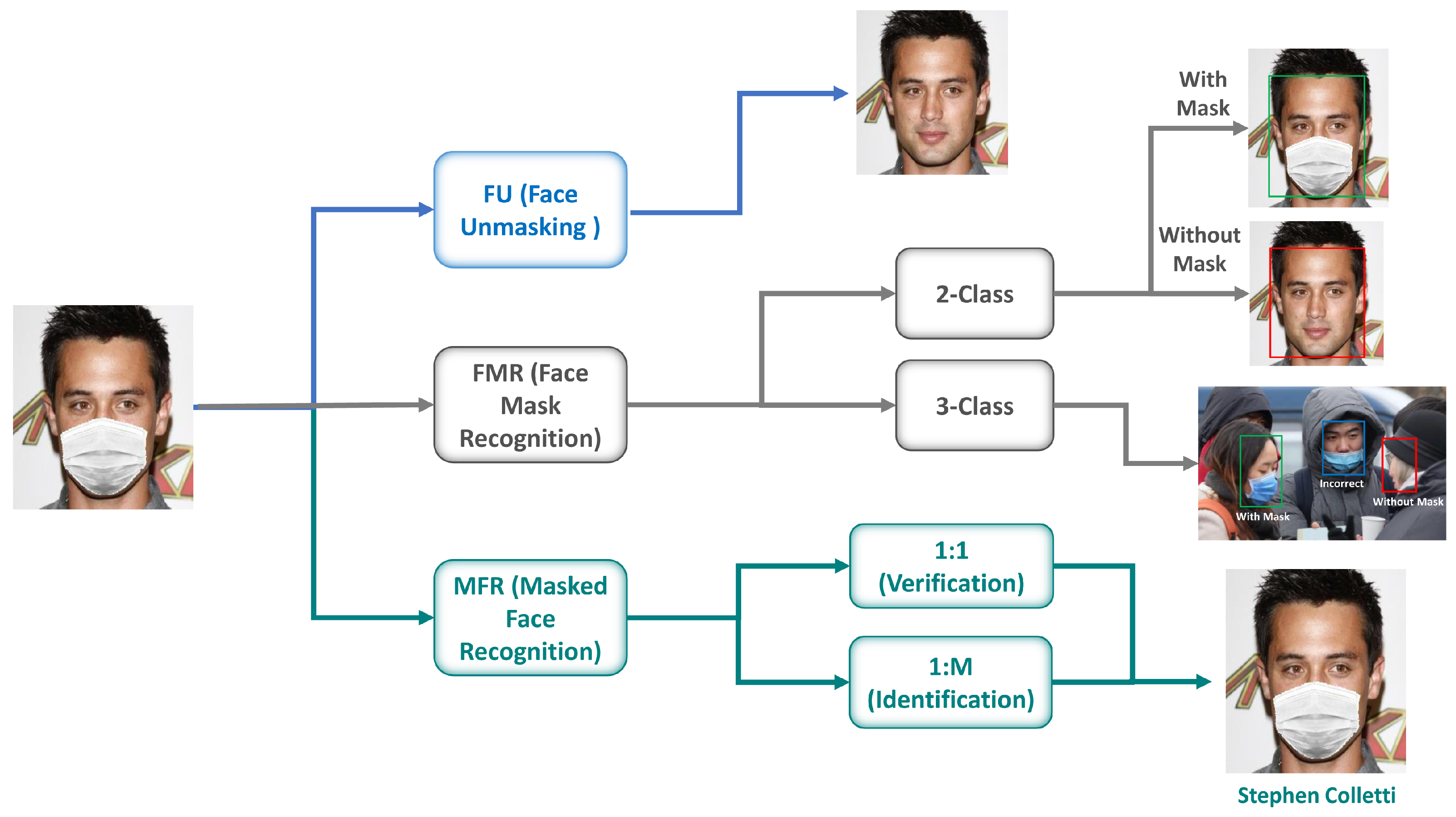
The Technical Challenge of Masked Face Recognition
Traditional face recognition systems depend heavily on complete facial feature visibility for accurate identification. Masks obscure critical regions including the nose, mouth, and lower cheeks – areas that contain distinctive identifying characteristics. This occlusion disrupts the feature patterns that conventional algorithms are trained to recognize, leading to potential performance degradation. Addressing this challenge requires innovative approaches that either reconstruct missing facial features or focus more intensively on the remaining visible areas. One effective strategy involves training models specifically on datasets containing masked faces, enabling them to learn which visible features remain most discriminative. Alternative methods employ generative models that can intelligently infer occluded regions based on contextual information from visible areas. Advanced attention mechanisms allow models to dynamically prioritize the most informative facial regions, minimizing the impact of covered areas. Successfully overcoming masked face recognition challenges ensures the continued relevance of this technology in environments where facial coverings are common, from healthcare settings to security checkpoints.
Addressing Bias in Facial Recognition Systems
Bias in face recognition represents a critical ethical and technical concern that can lead to discriminatory outcomes. Research has demonstrated that many systems exhibit reduced accuracy for certain demographic groups, including people of color, women, and older adults. These disparities stem from multiple sources: imbalanced training data, algorithmic design choices, and evaluation methodologies. To build fairer systems, developers should implement comprehensive bias mitigation strategies. Using diverse, representative training data that accurately reflects target populations is fundamental. This requires intentional data collection from varied sources across different demographics. Additionally, employing fairness-aware algorithms specifically designed to reduce bias through techniques like data re-weighting, regularization, or adversarial training can significantly improve equity. Regular assessment using fairness metrics – including equal opportunity, equalized odds, and demographic parity – provides quantitative measures of system performance across different groups. Continuous monitoring and auditing ensure that systems maintain fairness as they encounter new data and scenarios in production environments.
Building a Masked Face Recognition Model
Proper environment configuration forms the foundation for successful model development. Begin by installing essential Python packages that provide the computational, image processing, and machine learning capabilities required for face recognition tasks. Key libraries include NumPy for numerical operations, Pandas for data manipulation, OpenCV for image processing, Matplotlib for visualization, and Keras for neural network implementation. The Pillow library handles image loading and manipulation, while Pickle enables model serialization for saving and loading trained systems. A correctly configured environment ensures all necessary tools are available for the subsequent development stages, from data preparation through model deployment. This setup provides the framework for implementing sophisticated AI APIs and SDKs that might integrate with your recognition system.
Step 1: Environment Setup and Library Configuration
High-quality, well-prepared data serves as the cornerstone of effective face recognition systems. This guide utilizes a modified version of the Labeled Faces in the Wild (LFW) dataset, augmented with simulated masked images to create realistic training examples. The standard LFW dataset contains labeled face photographs suitable for recognition tasks, but lacks masked examples. To address this limitation, we generate synthetic masked images by programmatically overlaying mask templates onto existing faces using image processing techniques like alpha blending and geometric transformations. This approach creates a balanced dataset containing both masked and unmasked examples, providing the variation necessary for models to learn robust feature representations. Proper dataset preparation involves multiple stages: loading images with corresponding labels, resizing to consistent dimensions, normalizing pixel values, and partitioning into training and validation subsets. Meticulous data preparation directly influences model performance, ensuring the system receives high-quality, representative examples that enable effective learning across varied conditions.
Step 2: Comprehensive Dataset Preparation
The FaceNet model, developed by Google researchers, provides a powerful pre-trained foundation for face recognition tasks. This sophisticated convolutional neural network architecture generates compact face embeddings – dense vector representations that capture distinctive facial characteristics in a low-dimensional space. These embeddings enable efficient face verification, identification, and clustering operations. Loading the pre-trained FaceNet model involves importing both the network architecture and learned weights, then configuring it for feature extraction rather than full retraining. This transfer learning approach leverages knowledge acquired from massive face datasets, reducing development time and computational requirements. The model processes face images to produce 128-dimensional or 512-dimensional embeddings that serve as input features for subsequent classification stages. FaceNet's efficiency makes it suitable for deployment in resource-constrained environments, including edge devices and mobile applications. By building upon this established foundation, developers can focus on adapting the system for masked face scenarios rather than training from scratch.
Step 3: Implementing the FaceNet Model
With face embeddings extracted using FaceNet, the next stage involves building a classifier that maps these numerical representations to specific identities. This guide employs a Support Vector Machine (SVM) classifier, a robust algorithm well-suited for high-dimensional feature classification. SVMs work by identifying the optimal hyperplane that maximally separates different classes in the feature space. Training the classifier involves feeding it the face embeddings alongside their corresponding identity labels from the training dataset. The SVM learns the distinctive patterns associated with each individual, enabling it to accurately classify new, unseen examples. Critical preprocessing steps include L2 normalization of embeddings to ensure consistent feature scales and label encoding to convert textual identities to numerical values. Proper classifier training and validation ensure the system can reliably distinguish between individuals based on their facial characteristics, even when portions of the face are obscured by masks. This classification layer represents where many AI automation platforms would integrate the recognition capability into broader security or identification workflows.
Step 4: Classifier Development and Training
Thorough testing with previously unseen images provides the ultimate validation of model performance and generalization capability. This critical phase involves loading new images – both masked and unmasked – that the model hasn't encountered during training. The testing process mirrors the preprocessing pipeline: images are resized, normalized, and processed through the FaceNet model to generate embeddings. These embeddings then pass through the trained SVM classifier to produce identity predictions. Comparing these predictions against ground truth labels quantifies model accuracy across different conditions. Testing specifically with masked images evaluates the system's robustness to occlusions, while unmasked tests establish baseline performance. Comprehensive evaluation should include metrics beyond simple accuracy, such as precision, recall, and F1-score, particularly for imbalanced datasets. This rigorous testing methodology ensures the model performs reliably in real-world deployment scenarios, providing confidence in its practical applicability for security, access control, or identification systems.
Real-World Applications and Implementation Considerations
Masked face recognition technology finds applications across numerous sectors where identification remains essential despite facial coverings. In healthcare environments, the technology enables secure access control while accommodating medical mask requirements. Security checkpoints at airports and government facilities benefit from maintained identification capabilities during public health mandates. Retail security systems can continue monitoring despite customers wearing masks, while financial institutions preserve authentication processes for masked individuals. The technology also supports biometric security systems in corporate environments where mask policies may fluctuate. Each application domain presents unique requirements regarding accuracy thresholds, processing speed, and integration with existing security infrastructure. Understanding these varied use cases helps developers tailor systems to specific operational contexts and performance expectations.
Diverse Industry Applications
Successful implementation of masked face recognition requires careful consideration of system architecture and technical components. The complete pipeline typically includes face detection, alignment, feature extraction, and classification stages. For masked face scenarios, additional preprocessing steps may involve mask detection and specialized alignment techniques that focus on upper facial regions. System architects must balance accuracy requirements against computational constraints, particularly for real-time applications. Cloud-based deployments offer scalability and easy updates, while edge computing provides privacy advantages and reduced latency. Integration with existing security systems often requires standardized APIs and compatibility with legacy infrastructure. Performance monitoring and continuous improvement mechanisms ensure systems maintain accuracy as new mask styles and facial covering trends emerge. These architectural decisions significantly impact the practicality and effectiveness of deployed systems across different operational environments.
Technical Implementation and System Architecture
Optimizing masked face recognition systems involves multiple strategies to enhance accuracy while managing computational resources. Data augmentation techniques specifically tailored for masked scenarios – including varied mask positions, types, and colors – improve model robustness. Transfer learning approaches fine-tune pre-trained models on masked face datasets, accelerating development while maintaining performance. Ensemble methods that combine multiple algorithms can boost accuracy by leveraging complementary strengths. Attention mechanisms that dynamically weight facial regions help systems focus on the most discriminative visible features. Regular model retraining with newly collected data prevents performance degradation over time. These optimization techniques enable developers to create efficient, accurate systems suitable for practical deployment across diverse real-world scenarios, from high-security facilities to public venues.
Performance Optimization Techniques
Ethical Considerations and Responsible Deployment
The deployment of masked face recognition systems raises important privacy considerations that require careful attention. Organizations must implement transparent data handling practices, clearly communicating how facial data is collected, stored, and processed. Secure encryption of both stored templates and data in transit protects against unauthorized access. Establishing data retention policies that limit storage duration reduces privacy risks. Providing opt-out mechanisms where feasible respects individual autonomy while maintaining security where absolutely necessary. These privacy safeguards help balance security benefits with fundamental rights, fostering public trust in the technology's responsible use across different contexts and applications.
Privacy Protection and Data Security
Navigating the evolving regulatory landscape represents a critical aspect of responsible masked face recognition deployment. Different jurisdictions have implemented varying requirements regarding biometric data collection and processing. The European Union's GDPR establishes strict guidelines for biometric data handling, while various US states have enacted their own biometric privacy laws. Compliance involves implementing data protection impact assessments, obtaining appropriate consent where required, and maintaining comprehensive documentation of data processing activities. Adherence to emerging technical standards ensures interoperability and facilitates third-party auditing. Proactive compliance efforts not only meet legal obligations but also demonstrate organizational commitment to ethical technology practices, potentially enhancing public acceptance and trust.
Regulatory Compliance and Standards
Pros and Cons
Advantages
- Enables reliable identification despite partial facial occlusion
- Enhances security in environments where masks are commonly worn
- Adapts to evolving public health and safety requirements
- Integrates seamlessly with existing face recognition infrastructure
- Opens new applications in healthcare and medical settings
- Maintains functionality during seasonal mask usage periods
- Provides continuity of service during public health emergencies
Disadvantages
- Generally lower accuracy compared to unmasked recognition systems
- Requires specialized training datasets with masked examples
- Increased computational requirements for complex occlusion handling
- Raises additional privacy concerns with masked identification
- Potential vulnerability to adversarial attacks exploiting occlusions
Conclusion
Masked face recognition represents a crucial adaptation of biometric technology to contemporary realities where facial coverings have become commonplace. By leveraging advanced deep learning approaches, comprehensive dataset preparation, and thoughtful system design, developers can create robust identification systems that maintain functionality despite partial facial occlusions. The technical implementation pathway provides a practical framework for building effective solutions. However, successful deployment requires equal attention to ethical considerations, bias mitigation, and regulatory compliance. As the technology continues evolving, ongoing refinement will further enhance accuracy and expand applicable use cases. When implemented responsibly, masked face recognition technology offers valuable capabilities for security, access control, and identification across diverse sectors.
Frequently Asked Questions
How accurate is face recognition with masked images?
Modern masked face recognition systems can achieve over 90% accuracy with proper training data and algorithms. Performance depends on dataset quality, model architecture, and the specific visible features available. Systems trained on diverse masked datasets typically outperform those adapted from standard recognition models.
What are the main ethical concerns with face recognition?
Key ethical concerns include privacy violations, demographic bias, potential misuse by authorities, and lack of consent. Responsible deployment requires transparency, bias mitigation, regulatory compliance, and clear usage guidelines to balance security benefits with individual rights protection.
Can existing face recognition systems handle masks?
Standard systems experience significant accuracy drops with masks. Effective masked recognition requires retraining with masked datasets, specialized feature extraction focusing on upper face regions, and often architectural modifications to handle occlusion patterns specifically.
What types of masks are most challenging for face recognition?
Solid-colored masks covering the nose and mouth pose the greatest challenge, while transparent or partial masks may allow better feature extraction. Systems trained on diverse mask types perform more robustly across different masking scenarios.
How can organizations ensure ethical use of masked face recognition?
Organizations should implement transparency policies, obtain consent where possible, regularly audit for bias, comply with regulations, and use data minimization principles to protect privacy and ensure responsible deployment of the technology.
Relevant AI & Tech Trends articles
Stay up-to-date with the latest insights, tools, and innovations shaping the future of AI and technology.
Grok AI: Free Unlimited Video Generation from Text & Images | 2024 Guide
Grok AI offers free unlimited video generation from text and images, making professional video creation accessible to everyone without editing skills.
Grok 4 Fast Janitor AI Setup: Complete Unfiltered Roleplay Guide
Step-by-step guide to configuring Grok 4 Fast on Janitor AI for unrestricted roleplay, including API setup, privacy settings, and optimization tips
Top 3 Free AI Coding Extensions for VS Code 2025 - Boost Productivity
Discover the best free AI coding agent extensions for Visual Studio Code in 2025, including Gemini Code Assist, Tabnine, and Cline, to enhance your